The GridPlus Lattice1 hardware wallet could have helped prevent the $1.5 billion Bybit hack - a security breach that exploited weaknesses in how transactions are approved in crypto wallets. The effectiveness of this exploit, like others before it, relied on users being unable to verify what they are signing on a secure device. GridPlus pioneered Clear Signing for smart contract chains to address this specific vulnerability.
In this attack, the web-based interface of Safe, an industry-standard multi-signature smart contract wallet, was compromised by attackers who targeted the exchange. All transactions required that majority of those with authority to approve transactions for the account sign in software then approve the same request a second time using a hardware wallet. However, the tools they used did not provide Clear Signing and instead displayed a string of characters called a hash which could have been spoofed in the hacked Safe user interface.
The Lattice1’s secure touchscreen would have shown the actual recipient’s address. This would have allowed the Bybit team to see their account’s full balance was being sent to an unknown address. Using address labels would have made the discrepancy even easier to spot.
This is a core security benefit of hardware wallets: an assurance that you can view precisely what you are approving even when your phone, computer, or other tools are compromised.
In this post we're going to cover how all this fits together: blind signing, the details of the hack, and why secure hardware is the most important piece of addressing this kind of attack.
What is Blind Signing and Why Is It Dangerous?

Blind signing refers to approving a blockchain signing request without seeing or understanding its details. This takes place when you click through a transaction without reading it or when your hardware wallet does not display information that can be used to verify the accuracy of what your computer or phone displays.
Blind signing bypasses the security benefit of using a hardware wallet. It’s like installing a home security system and never turning it on.
Blind signing allows attackers to modify transaction details without detection.
Without being able to compare your software wallet against the secure display of a separate device, users have no way of verifying a recipient address or amount.
How GridPlus’ Smart Contract Clear Signing Enhances Crypto Security

GridPlus introduced the world's first hardware Clear Signing for Ethereum and EVM chains in January of 2021. By the end of 2023, GridPlus also introduced hardware Clear Signing for Solana.
Early hardware wallets were designed for Bitcoin and similar chains, where only recipient addresses needed verification. This approach protected against real-world attacks such as when the Tor privacy network was compromised for over a year and compromised relays replaced unencrypted crypto addresses with an attacker’s address. However, this limited approach fails with complicated smart contract transactions, where attackers can alter contract calls, permissions, and destinations.
As early Ethereum users, the GridPlus team immediately recognized this problem. So, we developed our own solution: hardware ABI parsing. This approach decoded transactions with results which more closely matched what you see in your software wallet for comparison. We deployed this technology on our flagship product, the Lattice1, which is the world’s first secure touchscreen hardware wallet.
The Lattice1 and Clear Signing addressed smart contract blind signing in hardware for the first time ever. This last line of defense requires users to actively look and compare the two requests. If they do not match, it indicates something is wrong and that the signing request should not be approved.
Unfortunately, the behaviors users learned from legacy tools have become the norm: everyone has become accustomed to blind signing since the most popular tools don’t actually let us see what we're signing.
How The Bybit Hack Unfolded

On February 21, 2025, the Bybit cryptocurrency exchange initiated a routine transfer from a Safe smart contract wallet. Unbeknownst the team, attackers had compromised a Safe developer’s computer and replaced the Safe web user interface with a malicious version.
This malicious UI displayed the transaction the Bybit team had intended to sign, but a fraudulent transaction request was sent to their hardware wallets.
This request sent the full contents of the address to an attacker’s receiving address - over 400,000 ETH.
There were many risk mitigation steps both parties could have taken, but with the tools they were using, they had no chance of detecting the mismatch and protecting themselves.
The outcome would have been the same whether they just blind signed by approving the transaction without looking at their hardware wallet or they actually checked its hash, because the hash could have been easily spoofed in the malicious UI. The team signed away $1.5B because they could not read what they were signing and had no way of knowing there was a problem.
Signing security with the Lattice1 would have given them a chance to identify that there was a problem. If just one of the signers checked the screen and compared against the Safe UI, they would have seen the recipient address was wrong.
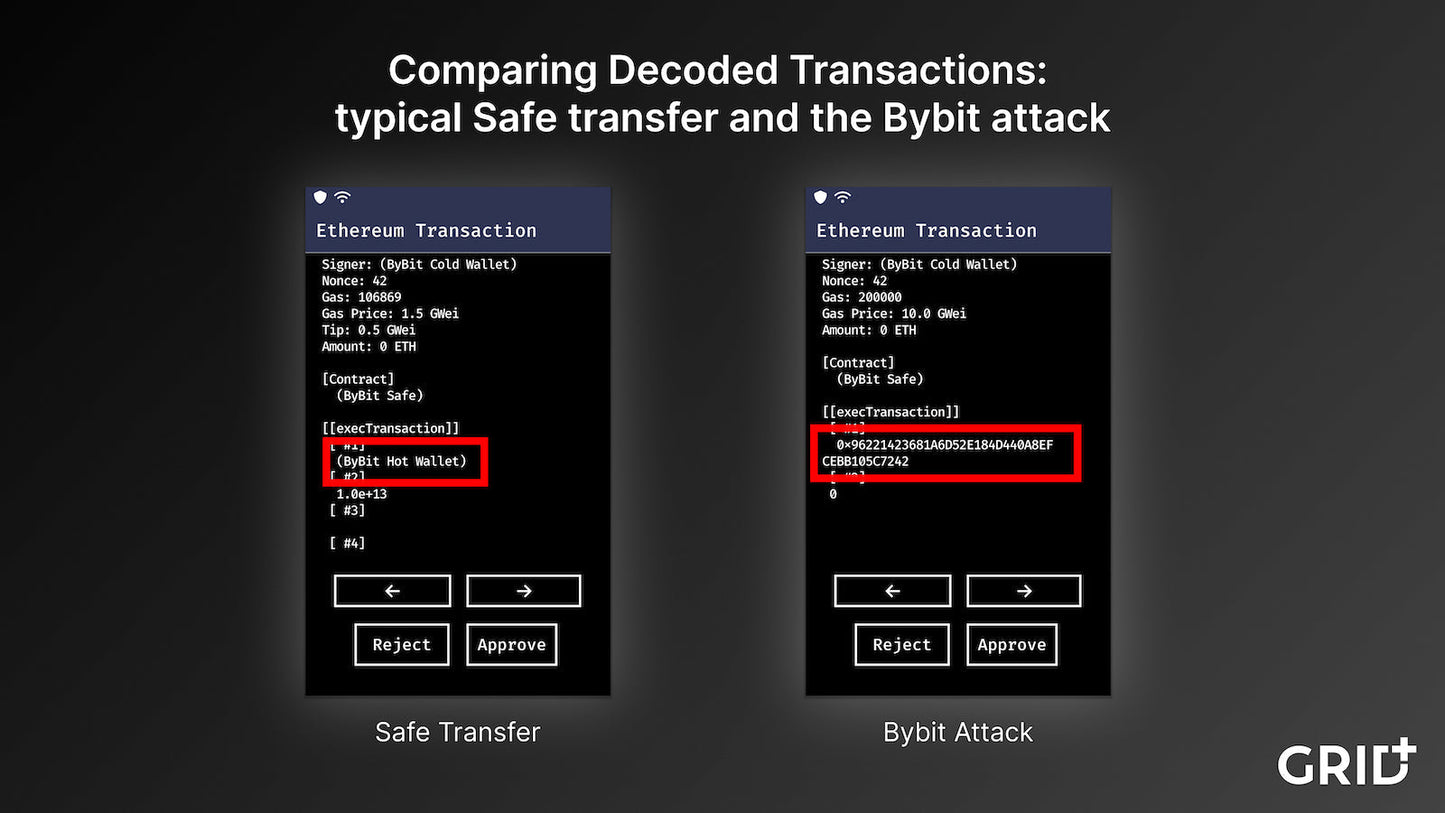
How the Signing Requests Would Have Appeared on The Lattice1

The GridPlus team reviewed the malicious signing payload and replicated the signing request from the attack on a Lattice1 hardware wallet in a safe environment. The images above are a comparison of a standard Safe signing request and the malicious payload.
In this example Lattice1 account labels are used; this is an optional step. It is important to note that these labels would be stored locally so they could not be replicated by a remote attacker.
The most important thing to note is the recipient address, which could be compared against the signing request in the Safe UI.
That’s it. Just one of the signers checking the recipient address could have made a difference.
The Bybit attack and others like it such as the $50M Radiant Finance hack were predicated on a key assumption by the attackers: the victims would not be able to see the fraudulent signing request on on their hardware wallets.
What GridPlus is Doing to Improve Crypto Security for Everyone

GridPlus is actively developing new solutions to make crypto transactions safer and easier to verify.
By verifying a few key details such as recipient address, contract address, or transaction amounts, Lattice1 users can avoid signing many dangerous transaction requests, but the information that is displayed appears complicated for many users. GridPlus pioneered hardware Clear Signing and we’re glad to see other manufacturers begin to follow suit in this area, but it’s only the first step.
Today, we are focusing on several improvements in parallel:
- Plain-Language Transaction Summaries for human-readable explanations of signing requests.
- Parallel Transaction Simulation for comparing expected vs actual outcomes of approving a signing request.
- Strong Visual Verification for instant cues to quickly detect inconsistencies between signing requests displayed in your software and hardware wallets.
- Industry Collaboration with our partners to make it easier for everyone to keep themselves safer.
- New Approaches to Secure Hardware to mitigate the risk of man-in-the-middle attacks.
Readable transactions aren’t important just for better user experiences - understanding what you’re doing is essential for security. The mission-critical data you see on your Lattice1’s screen is backed either by a proof or by cross-referencing multiple external sources. We hope to deliver these improvements for our users with the same assurances that come with our decoded transactions today.
A major shift is coming to the crypto user experience with new tools like AI agents, programmable smart contract wallets that automate signing tasks for you, and more. GridPlus is collaboratively exploring advancements which will make blockchains safer for everyone while also making them more accessible without requiring technical expertise.
Why Is Secure Hardware Critical In Addressing Blind Signing?

Preventing attacks like the Bybit hack requires a shift in security priorities - software solutions alone cannot provide adequate protection.
There are many great teams working to mitigate user risk on the software side, but all software solutions fail when a computer or phone is compromised with malware because there is no assurance that what you are seeing is what you are actually signing.
Arguably, the crypto ecosystem has over-indexed software solutions because our common hardware tools remain ill-suited to how users sign today and hardware development is complicated. Wallet software remains susceptible to malware, phishing, social engineering, UI manipulations, and supply chain attacks leveraging compromised dependencies.
Physically isolated, tamper-resistant hardware with a secure display remains the true last line of defense, as it ensures that transaction details are verified independently of the host device.
What Else Could Have Helped Prevent the Bybit Hack?
There are many other ways in which the Safe team, security professionals, and wallet teams are responding to the severity of the threat laid bare by the Bybit hack.
Exchanges and blockchain companies should engage security professionals for a thorough review of internal control procedures, operational security, and key management. Steps such as using dedicated computers for critical tasks to limit exposure to malware and other attack vectors combined with formalizing security policies across an organization will mitigate risk.
For regular users, hardware and software wallet teams are coordinating on safer and more intuitive signing flows that make it easier to see if something is amiss at a glance. Efforts are underway to deprecate dangerous and rarely used signing standards which are sometimes used by hackers to obscure the purpose of a signing request.
A comprehensive guide to security best practices suitable for different types of user is outside the scope of this piece, but the GridPlus team will continue to share educational content and highlight independent guides and tools for keeping your crypto secure.
Final Thoughts & How to Get In Touch
The Bybit hack was a much needed wakeup call for an industry that moves fast and sometimes treats security as a secondary consideration - thankfully, many are rising to the occasion to collaboratively improve the tools we rely on with our money every day.
The GridPlus team believes that more comprehensive solutions to make crypto safer for everyone will require industry collaboration. We are already working with our software wallet partners on improvements. If you are a security professional, work on a wallet, want to collaborate on an industry standard, or just have ideas you’d like to share please reach out to us directly.
Learn more about GridPlus at gridplus.io. Additionally, Discord or Twitter can be used as a switchboard to connect to the right resources.
If you’re a regular user with questions about this piece, Clear Signing, private key management, or crypto security in general we always do our best to make ourselves available on Discord, so please come say hello to the team!
If you believe any part of this piece should be revised for accuracy based on the published details of the hack, let us know. The Safe team’s investigation in partnership with Mandiant is ongoing, and we will update this post as needed as further information comes to light.
Let’s build a safer future for all crypto users together.
